Which operating system do ‘professional’ hackers use?
Which operating system do ‘real’ hackers use?
Which operating system do the ‘real’ hackers use? The real here is the cyber criminal type hackers and...
Skills Required to Become an Ethical Hacker
Skills allow you to achieve your desired goals within the available time and resources. As a hacker, you will need to develop skills that...
Man-in-the-Middle Tutorial: Learn About Man-in-the-Middle Attacks, perform man in the middle...
Man-in-the-Middle Attacks: ARP Poisoning
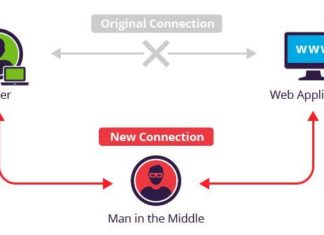
What is Man-in-the-Middle Attack?
In cryptography and computer security, a man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and...
5 Best WiFi Hacking Tools
These are the popular tools used for wireless password cracking and network troubleshooting.
1. AirSnort WiFi Hacking Tool
AirSnort is another popular tool for decrypting WEP encryption on the Wi-Fi...
Hack WPA/WPA2 Wi-Fi With Kali Linux & Aircrack-ng
Kali Linux can be used for many things, but it probably is best known for its ability to penetration test, or “hack,” WPA and...
How to Install Kali Linux on PC / Laptop Hard Disk
If you want to learn Kali Linux. First You Need to Install Kali Linux in Your Computer / Laptop.
You can Install Linux in Two...