Man-in-the-Middle Attacks: ARP Poisoning
What is Man-in-the-Middle Attack?
In cryptography and computer security, a man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. One example of man-in-the-2 attacks is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within reception range of an unencrypted wireless access point (Wi-Fi) can insert himself as a man-in-the-middle.
 As an attack that aims at circumventing mutual authentication, or lack thereof, a man-in-the-middle attack can succeed only when the attacker can impersonate each endpoint to their satisfaction as expected from the legitimate ends. Most cryptographic protocols include some form of endpoint authentication specifically to prevent MITM attacks. For example, TLS can authenticate one or both parties using a mutually trusted certificate authority.
As an attack that aims at circumventing mutual authentication, or lack thereof, a man-in-the-middle attack can succeed only when the attacker can impersonate each endpoint to their satisfaction as expected from the legitimate ends. Most cryptographic protocols include some form of endpoint authentication specifically to prevent MITM attacks. For example, TLS can authenticate one or both parties using a mutually trusted certificate authority.
Man-in-the-middle (MITM) attacks are a valid and extremely successful threat vector. Exploitation usually needs knowledge of various tools and physical access to the network or proximity to an access point. MITM attacks usually take advantage of ARP poisoning at Layer 2, even though this attack has been around and discussed for almost a decade.
An MITM attack can take a few different forms. ARP poisoning is the most popular, but DHCP, DNS, and ICMP poisoning are also effective, as well as the use of a malicious wireless access point (AP). Fake access points have become a common threat vector, exploiting the habit in which clients automatically connect to known SSIDs. This allows an attacker to connect and intercept the victim’s network traffic without the victim noticing any indication they are under attack. To hasten a connection, attacks against the legitimate access point can be made to help the malicious AP become the last AP standing.
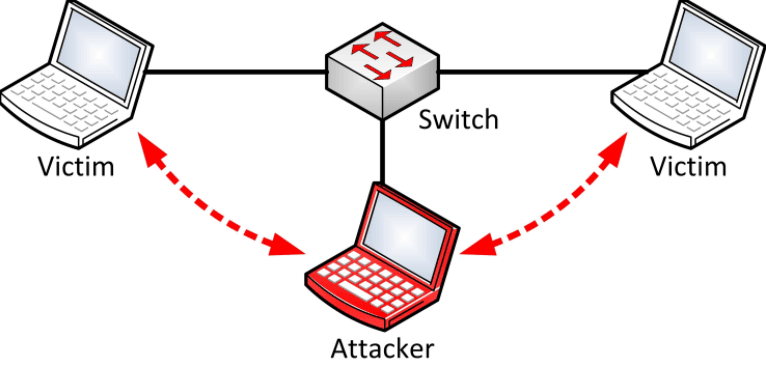
ARP poisoning works by simply replying to Address Resolution Protocol (ARP) requests with the attacker’s MAC address. The attacker tells the device that needs to communicate with the victim’s computer that the attacker knows how to reach the victim, and then the attacker tells the network that the attacker’s computer is the victim’s computer, completely masquerading as the victim’s computer and replying on its behalf. The switch then updates its table of MAC addresses with the attacker’s MAC address. The switch uses this to route traffic and now believes the attacker’s system is the victim’s system. This creates an MITM situation where the victim routes its traffic through the attacker and out through the gateway to wherever it needs to go.
How to perform Man In The Middle (MITM) Attack in Kali Linux
Currently, in this tutorial, we are going to perform the man in the middle attack using Kali Linux.
The man-in-the-middle attack (often abbreviated MITM, MitM, MIM, MiM, MITMA) in cryptography and computer security is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker.
Victim IP address: 192.168.8.90
Attacker network interface: eth0; with IP address: 192.168.8.93
Router IP address: 192.168.8.8
Requirements:
- Arpspoof
- Driftnet
- Urlsnarf
Step by step Kali Linux Man in the Middle Attack :
- Open your terminal (CTRL + ALT + T Kali shortcut) and configure our Kali Linux machine to allow packet forwarding, because act as the man in the middle attacker, Kali Linux must act as the router between “real router” and the victim. Read the tutorial here how to set up packet forwarding in Linux.
- You can change your terminal interface to make the view much more friendly and easy to monitor by splitting Kali Linux terminal window.
- The next step is setting up arp-spoof between victim and router.
arpspoof -i eth0 -t 192.168.8.90 192.168.8.8
- And then setting up arpspoof from to capture all packet from the router to victim.
arpspoof -i eth0 192.168.8.8 192.168.8.90
- After step three and four, now all the packet sent or received by victim should be going through attacker machine.
- Now we can try to use driftnet to monitor all victim image traffic. According to its website.
Driftnet is a program which listens to network traffic and picks out images from TCP streams it observes. Fun to run on a host which sees lots of web traffic.
- To run driftnet, we just run this
driftnet -i eth0
When victim browse a website with the image, driftnet will capture all image traffic as shown in the screenshot below.
To stop driftnet, just close the driftnet window or press CTRL + C in the terminal
- For the next step we will try to capture the website information/data by using urlsnarf. To use urlsnarf, just run this code
urlsnarf -i eth0
and urlsnarf will start capturing all website address visited by victim machine.
- When victim browse a website, the attacker will know the address victim visited.
Man-in-the-Middle Attack Examples
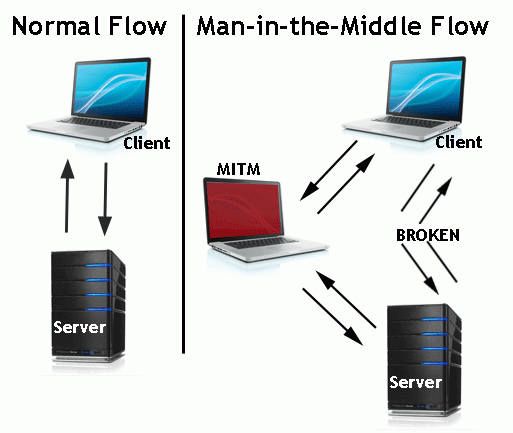
In the image above, you will notice that the attacker inserted him/herself in-between the flow of traffic between client and server. Now that the attacker has intruded into the communication between the two endpoints, he/she can inject false information and intercept the data transferred between them.
Below is another example of what might happen once the man in the middle has inserted him/herself.
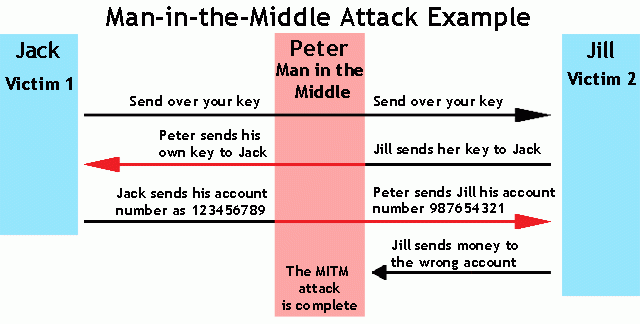
The hacker is impersonating both sides of the conversation to gain access to funds. This cyber attack holds true for a conversation with a client and server as well as person-to-person conversations. In the example above, the attacker intercepts a public key and with that can transpose his own credentials to trick the people on either end into believing they are talking to one another securely.





WOW jus what I was looking for. Came here by searching for
see this