How to stop windows update in windows 10 | How to...
Windows 10 software updates install on your device automatically (whether you like it or not), but this guide can help you retake control and...
Windows 10 Keyboard Shortcuts Cheat Sheet
Windows 10 Keyboard Shortcuts Cheat Sheet
Turning multiple mouse clicks into a simple press of a key or two may not seem like a lot,...
100+ Hacking Tools To be Pro Hacker – Free Download
Wireless Hacking Tools
Wireless Hacking Tools are those hacking tools which are used to hack into a wireless network which is usually more susceptible to...
How to send WhatsApp Message without saving contact number on your...
How to send a WhatsApp chat without saving the contact
Now I show you how you can send WhatsApp Message without saving any contact number...
How to find that your smartphone has been hacked and How...
Smartphones are almost always connected to the internet, so it stands to reason that your phone hacked remotely. Hackers are always out there looking...
How to Install fonts on Kali Linux – Microsoft TrueType core...
Installing fonts is important for those who are multilingual or want to spice up their screen. Many websites use different fonts and without having...
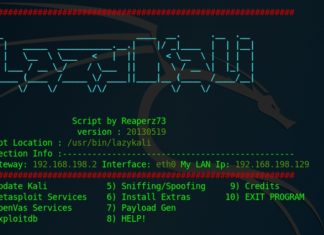
How to install LazyKali and HackPack Script in Kali Linux
You learn Installing LazyKali and HackPack Script in Kali Linux. Also basic information about LazyKali and HackPack Script. This is a collection of scripts to add...
Different Types Of DDoS Attacks Used By Hackers
What is Distributed Denial of Service(DDoS) attack?
Distributed Denial of Services is a type of cyber attack that is mostly used by hackers to take...