What to do with your old laptop
Introduction
Every day, there is a need for new technology or new things. If we talk about professional working, there is a need for new...
How to find that your smartphone has been hacked and How...
Smartphones are almost always connected to the internet, so it stands to reason that your phone hacked remotely. Hackers are always out there looking...
Skills Required to Become an Ethical Hacker
Skills allow you to achieve your desired goals within the available time and resources. As a hacker, you will need to develop skills that...
How to stop windows update in windows 10 | How to...
Windows 10 software updates install on your device automatically (whether you like it or not), but this guide can help you retake control and...
A To Z List of Linux Commands | All Linux commands...
Linux distributions can leverage an extensive range of commands to accomplish various tasks. For most Linux distros, Bash (Bourne again shell) is the default...
ls Command in Linux / Unix with Example
ls command is one of the most frequently used commands in Linux. I believe ls command is the first command you may use when...
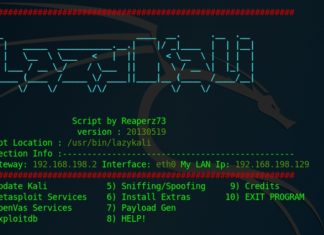
How to install LazyKali and HackPack Script in Kali Linux
You learn Installing LazyKali and HackPack Script in Kali Linux. Also basic information about LazyKali and HackPack Script. This is a collection of scripts to add...
How to see who likes who on Instagram?
Instagram's multifunctionality forces users to use it for a variety of purposes. Some users are active on their profiles, promoting and becoming famous. While...