ls Command in Linux / Unix with Example
ls command is one of the most frequently used commands in Linux. I believe ls command is the first command you may use when...
What is Linux?
Linux is the best-known and most-used open-source operating system. As an operating system, Linux is software that sits underneath all of the other software...
A To Z List of Linux Commands | All Linux commands...
Linux distributions can leverage an extensive range of commands to accomplish various tasks. For most Linux distros, Bash (Bourne again shell) is the default...
How to Install fonts on Kali Linux – Microsoft TrueType core...
Installing fonts is important for those who are multilingual or want to spice up their screen. Many websites use different fonts and without having...
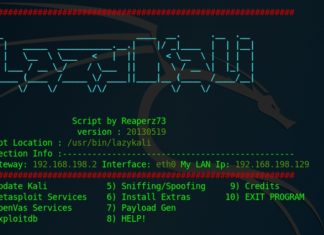
How to install LazyKali and HackPack Script in Kali Linux
You learn Installing LazyKali and HackPack Script in Kali Linux. Also basic information about LazyKali and HackPack Script. This is a collection of scripts to add...
Which operating system do ‘professional’ hackers use?
Which operating system do ‘real’ hackers use?
Which operating system do the ‘real’ hackers use? The real here is the cyber criminal type hackers and...
Man-in-the-Middle Tutorial: Learn About Man-in-the-Middle Attacks, perform man in the middle...
Man-in-the-Middle Attacks: ARP Poisoning
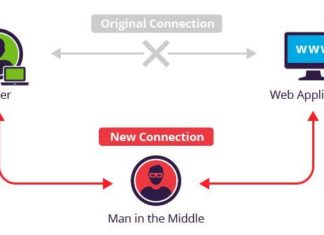
What is Man-in-the-Middle Attack?
In cryptography and computer security, a man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and...
Hack WPA/WPA2 Wi-Fi With Kali Linux & Aircrack-ng
Kali Linux can be used for many things, but it probably is best known for its ability to penetration test, or “hack,” WPA and...