Tag: Kali Linux
Which operating system do ‘professional’ hackers use?
Which operating system do ‘real’ hackers use?
Which operating system do the ‘real’ hackers use? The real here is the cyber criminal type hackers and hacktivists and not security researchers and white hat hackers. You can call these ‘real’ hackers black or gray hat hackers as they use their skill sets against the government, media organizations, and companies either for...
Man-in-the-Middle Tutorial: Learn About Man-in-the-Middle Attacks, perform man in the middle attack in Kali Linux, ARP Poisoning
Man-in-the-Middle Attacks: ARP Poisoning
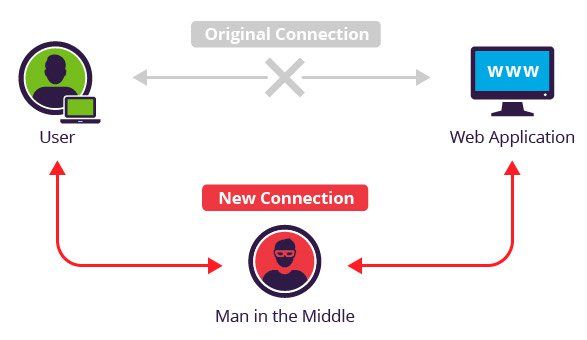
What is Man-in-the-Middle Attack?
In cryptography and computer security, a man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other. One example of man-in-the-2 attacks is active eavesdropping, in which the attacker makes independent connections with the victims and...
How to Install Kali Linux on PC / Laptop Hard Disk
If you want to learn Kali Linux. First You Need to Install Kali Linux in Your Computer / Laptop.
You can Install Linux in Two ways
By Virtual Machine
By Direct install on your PC
Kali Linux installation process
Now I show you how you can install Kali Linux directly on your PC / Laptop Hard...